"IT Solutions That Power Your Growth — Fast, Secure, and Tailored for Australian Businesses."
"We help SMBs scale with secure, responsive IT services that reduce downtime, simplify compliance, and strengthen cyber resilience."
"IT Solutions That Power Your Growth — Fast, Secure, and Tailored for Australian Businesses."
"We help SMBs scale with secure, responsive IT services that reduce downtime, simplify compliance, and strengthen cyber resilience."
Personalised, Reliable, and Ethical IT Services for Australian Businesses
Our Story:
Meet Hendrik van Zyl — Founder & Principal Consultant
Hendrik van Zyl, Founder — supporting Australian businesses since 1993
Personalised, Reliable, and Ethical IT Services for Australian Businesses
Our Story:
From humble beginnings in a home office over thirty years ago, we've built our company on a foundation of technical excellence and genuine care for Australian businesses.
What started as a passion project has evolved into a trusted technology partner for businesses across Australia, while maintaining the personalized approach only a family-owned operation can deliver.
We see our clients as extensions of our own family. Every solution we provide, every challenge we solve, strengthens relationships that transcend typical business partnerships—creating a community of growth, achievement, and shared success.
Our Services
Comprehensive IT Support
Multi-Channel Support
Dedicated Help Desk
Secure Customer Portal
Education & Training
Infrastructure Design & Build
Strategic Planning
Consulting Services
Change Managment
IT Budget Costing
Business Continuity Planning
Disaster Recovery Solutions
IT Resilience Planning
Data Backup and Protection
Business Impact Analysis
High Speed Internet.
Virtual Private Network (VPN)
Wireless Networks
IP Phone Systems (VoIP)
Identity and Access Management
Compliance and Governance
Network Security
Email Security
Security Awareness Education

Resources
Debunking 17 Myths on Network Security
Many businesses approach network security like making a fortress made out of pillows, chairs, and blankets. But the internet is a much scarier place than one’s living room. And many businesses neglect their security measures, leaving their data exposed to cyber threats.
This negligence often leads to costly breaches and operational disruptions.
In hopes to protect your business and keep you on your toes, we’re debunking common myths about network security to help safeguard your business effectively.

What is Network Security
Network security is the practice of protecting a computer network against unauthorised access, misuse, or theft. It combines multiple layers of defenses and creates a secure infrastructure for devices, applications, and users. It’s essential for maintaining the security of sensitive information and limits uninterrupted business operations.
Why Network Security is Important
Unless you want to have a system filled with bugs and potential threats, network security is something you don’t want to neglect. Below are some key reasons why:
Protects sensitive information from unauthorised access
Prevents costly cyberattacks
Safeguards customer trust
Certifies adherence to regulatory standards
Avoids operational disruptions
Mitigates financial losses

Network Security Myths Debunked
Now, let’s go over 17 common myths about network security and reveal the truth behind each one. Understanding these misconceptions will help you better shield your business and make wiser decisions about your network security strategy.
Small businesses aren't targets for cyberattacks: Small businesses are actually frequent targets because they often have weaker security measures, making them easier to exploit. In fact, 61% of small and medium-sized businesses (SMBs) were successfully attacked by cybercriminals in 2023.
Antivirus software alone is enough protection: Antivirus software is just one layer of defense and cannot protect against all types of cyber threats, such as phishing or ransomware attacks. Modern threats often require advanced detection systems and comprehensive security strategies.
Strong passwords are sufficient: As of June 20204, 4 million people around the globe still use "password" as the password for their accounts. Hopefully you're not one of them. And while important, strong passwords alone do not provide complete security. Cybercriminals can use techniques like phishing and keylogging to bypass even the strongest passwords. Multi-factor authentication (MFA) adds an essential extra layer of security.
Cyber Security is only an IT department issue: Cyber security is a company-wide responsibility that requires awareness and participation from all employees. For instance, regular training on recognising phishing emails can prevent breaches initiated by human error.
Firewalls alone provide complete security: Firewalls are just one component of a multi-layered security strategy. They need to be complemented with intrusion detection systems, regular software updates, and user education to be effective.
Security breaches are immediately noticeable: Many breaches can go undetected for long periods. For example, the Marriott data breach in 2014 went unnoticed for four years, exposing the personal information of 500 million guests.
Free security software offers the same protection as paid solutions: Free software often lacks the comprehensive features and support of paid solutions, such as advanced threat detection, regular updates, and customer support.
Cloud services are inherently insecure: Many cloud services offer robust security features, but they must be properly configured and managed. Misconfigurations, such as leaving cloud storage publicly accessible, have led to numerous data breaches.
Cyber Security is a one-time setup task: Effective cyber security requires continuous monitoring and updating. Cyber threats are constantly evolving, requiring ongoing adjustments to security strategies and tools.
Physical security measures are unnecessary: Physical access to network hardware can compromise security. For example, an intruder gaining physical access to a server room could install malicious hardware or software.
Mobile devices don't need the same security as desktops: Mobile devices are equally susceptible to cyber threats. They can be compromised through malware, phishing, and unsecured Wi-Fi networks, necessitating robust security measures.
Using a VPN makes you completely anonymous online: VPNs enhance privacy but do not guarantee complete anonymity. For example, if a user logs into their personal accounts while using a VPN, their identity can still be tracked.
Hackers only target financial data: Hackers target various types of sensitive information, not just financial data. Personal data, intellectual property, and medical records are also highly valuable and frequently targeted.
Security measures slow down business operations: Modern security solutions can be both efficient and effective. For instance, automated security systems and streamlined protocols can protect without significantly impacting productivity.
Social engineering attacks are easy to spot: Social engineering attacks can be highly sophisticated and difficult to detect. Cybercriminals often use detailed personal information to create convincing scams, such as spear-phishing emails.

Backup data doesn't need to be secured: Backup data is a prime target for cybercriminals and must be secured. Encrypting backups and storing them in secure locations can prevent unauthorised access and data breaches. Take a look at our Comprehensive Cloud Back Up & Recovery solutions.
Cyber insurance is unnecessary if you have strong security: Cyber insurance provides an additional layer of protection against potential financial losses from cyber incidents. It can help cover the costs of recovery, legal fees, and notification processes following a breach.

How to Implement Effective Network Security Measures
Implementing effective network security measures can seem like untangling knotted wire, but with the right approach and support, it can be manageable—even straightforward!
Here are seven practical steps to help you secure your business's data and operations.
1. Conduct a Comprehensive Security Audit
Start by assessing your current security posture and identifying areas for improvement. This baseline audit will serve as your roadmap, highlighting vulnerabilities and guiding your security strategy moving forward.
2. Implement Strong Access Controls
Certify that only authorized personnel have access to sensitive information. Implement multi-factor authentication and role-based access controls to restrict access and protect critical data.
3. Regularly Update and Patch Systems
Keep all software and systems up-to-date to protect against known vulnerabilities. Regular updates and patches are essential to close security gaps and defend against new threats.
4. Utilise Advanced Firewalls and Intrusion Detection Systems
Deploy firewalls to block unauthorised access and intrusion detection systems to monitor and respond to potential threats in real-time. These tools provide a robust defense against cyber attacks.
5. Educate and Train Your Employees
Security is a team effort. Regularly educate your employees about the latest cyber threats and best practices for maintaining security, such as recognising phishing attempts and following secure protocols.
6. Secure Mobile Devices and Remote Work Environments
Mobile devices and remote work setups should be protected with the same level of security as your main office. Use VPNs, encryption, and secure access protocols to safeguard data and communications.
7. Backup Data Regularly
Regularly backup your data to prevent loss in case of a cyberattack. Ensure that backups are encrypted and stored securely to protect against unauthorised access and data breaches. Take a look at our Comprehensive Cloud Back Up & Recovery solutions.
Leverage Advanced Security Tools
Another way to ensure effective network security is by using the correct tools. There are several amazing tools out there however, we use Lionguard which specializes in continuous attack surface management.
Liongard offers automated configuration change detection and detailed asset inventory, ensuring comprehensive visibility into your IT infrastructure. This tool helps detect misconfigurations, a common cause of cybersecurity issues, and provides timely alerts for swift resolutions.
By investing in the right tools, businesses can improve their security management, support compliance, and reduce the risk of cyber incidents, all while optimizing operational efficiency.
Conclusion
While it may not seem like a big deal, there have been several cases of businesses undergoing nightmare cyber threats, resulting in significant financial and reputational damage. That said, by conducting comprehensive audits, keeping systems updated, utilizing advanced security tools, and educating your team, you can create a more secure environment. If you need expert assistance and tailored solutions, reach out today! We’ll answer any questions you have on protecting your business.

Our Services
IT Support

Comprehensive IT Support
Proactive Maintenance & Monitoring
Multi-Channel Support
Dedicated Help Desk
Secure Customer Portal
Education & Training
Professional Services

Infrastructure Design & Build
Strategic Planning
Consulting Services
Change Managment
IT Budget Costing
SaaS

Cloud Data Protection - Microsoft 365, Google Workspace, Salesforce, Box, and Dropbox data
Windows, Mac & Linux Backup
Email Security
Anti-Virus & Anti-Malware
Business Continuity

Business Continuity Planning
Backup and Disaster Recovery
Remote Work Solutions
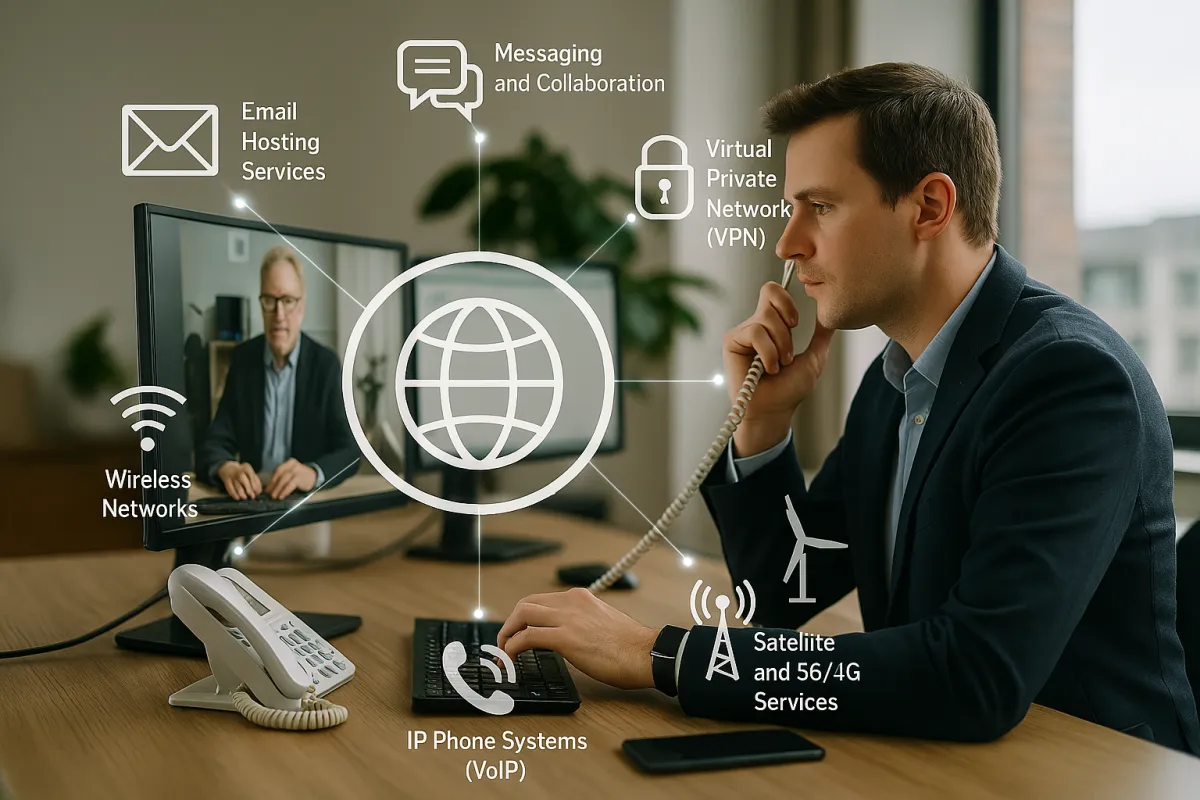
Communications

Email Hosting Services.
Messaging and Collaboration.
High Speed Internet.
Virtual Private Network (VPN)
Mobile Connectivity. Satellite and 5G/4G Services.
Wireless Networks
IP Phone Systems (VoIP)
Cybersecurity

Identity and Access Management
Compliance and Governance
Network Security
Email Security
Security Awareness Education
Continuous Cyber Risk Assessments
Resources
At Interdata Solutions, we understand the importance of staying ahead in today's dynamic business landscape.
That's why we offer valuable insights to our clients, providing them with the latest trends, market analyses, and expert perspectives tailored to the IT sector.

Debunking 17 Myths on Network Security
Many businesses approach network security like making a fortress made out of pillows, chairs, and blankets. But the internet is a much scarier place than one’s living room. And many businesses neglect their security measures, leaving their data exposed to cyber threats.
This negligence often leads to costly breaches and operational disruptions.
In hopes to protect your business and keep you on your toes, we’re debunking common myths about network security to help safeguard your business effectively.

What is Network Security
Network security is the practice of protecting a computer network against unauthorised access, misuse, or theft. It combines multiple layers of defenses and creates a secure infrastructure for devices, applications, and users. It’s essential for maintaining the security of sensitive information and limits uninterrupted business operations.
Why Network Security is Important
Unless you want to have a system filled with bugs and potential threats, network security is something you don’t want to neglect. Below are some key reasons why:
Protects sensitive information from unauthorised access
Prevents costly cyberattacks
Safeguards customer trust
Certifies adherence to regulatory standards
Avoids operational disruptions
Mitigates financial losses

Network Security Myths Debunked
Now, let’s go over 17 common myths about network security and reveal the truth behind each one. Understanding these misconceptions will help you better shield your business and make wiser decisions about your network security strategy.
Small businesses aren't targets for cyberattacks: Small businesses are actually frequent targets because they often have weaker security measures, making them easier to exploit. In fact, 61% of small and medium-sized businesses (SMBs) were successfully attacked by cybercriminals in 2023.
Antivirus software alone is enough protection: Antivirus software is just one layer of defense and cannot protect against all types of cyber threats, such as phishing or ransomware attacks. Modern threats often require advanced detection systems and comprehensive security strategies.
Strong passwords are sufficient: As of June 20204, 4 million people around the globe still use "password" as the password for their accounts. Hopefully you're not one of them. And while important, strong passwords alone do not provide complete security. Cybercriminals can use techniques like phishing and keylogging to bypass even the strongest passwords. Multi-factor authentication (MFA) adds an essential extra layer of security.
Cyber Security is only an IT department issue: Cyber security is a company-wide responsibility that requires awareness and participation from all employees. For instance, regular training on recognising phishing emails can prevent breaches initiated by human error.
Firewalls alone provide complete security: Firewalls are just one component of a multi-layered security strategy. They need to be complemented with intrusion detection systems, regular software updates, and user education to be effective.
Security breaches are immediately noticeable: Many breaches can go undetected for long periods. For example, the Marriott data breach in 2014 went unnoticed for four years, exposing the personal information of 500 million guests.
Free security software offers the same protection as paid solutions: Free software often lacks the comprehensive features and support of paid solutions, such as advanced threat detection, regular updates, and customer support.
Cloud services are inherently insecure: Many cloud services offer robust security features, but they must be properly configured and managed. Misconfigurations, such as leaving cloud storage publicly accessible, have led to numerous data breaches.
Cyber Security is a one-time setup task: Effective cyber security requires continuous monitoring and updating. Cyber threats are constantly evolving, requiring ongoing adjustments to security strategies and tools.
Physical security measures are unnecessary: Physical access to network hardware can compromise security. For example, an intruder gaining physical access to a server room could install malicious hardware or software.
Mobile devices don't need the same security as desktops: Mobile devices are equally susceptible to cyber threats. They can be compromised through malware, phishing, and unsecured Wi-Fi networks, necessitating robust security measures.
Using a VPN makes you completely anonymous online: VPNs enhance privacy but do not guarantee complete anonymity. For example, if a user logs into their personal accounts while using a VPN, their identity can still be tracked.
Hackers only target financial data: Hackers target various types of sensitive information, not just financial data. Personal data, intellectual property, and medical records are also highly valuable and frequently targeted.
Security measures slow down business operations: Modern security solutions can be both efficient and effective. For instance, automated security systems and streamlined protocols can protect without significantly impacting productivity.
Social engineering attacks are easy to spot: Social engineering attacks can be highly sophisticated and difficult to detect. Cybercriminals often use detailed personal information to create convincing scams, such as spear-phishing emails.

Backup data doesn't need to be secured: Backup data is a prime target for cybercriminals and must be secured. Encrypting backups and storing them in secure locations can prevent unauthorised access and data breaches. Take a look at our Comprehensive Cloud Back Up & Recovery solutions.
Cyber insurance is unnecessary if you have strong security: Cyber insurance provides an additional layer of protection against potential financial losses from cyber incidents. It can help cover the costs of recovery, legal fees, and notification processes following a breach.

How to Implement Effective Network Security Measures
Implementing effective network security measures can seem like untangling knotted wire, but with the right approach and support, it can be manageable—even straightforward!
Here are seven practical steps to help you secure your business's data and operations.
1. Conduct a Comprehensive Security Audit
Start by assessing your current security posture and identifying areas for improvement. This baseline audit will serve as your roadmap, highlighting vulnerabilities and guiding your security strategy moving forward.
2. Implement Strong Access Controls
Certify that only authorized personnel have access to sensitive information. Implement multi-factor authentication and role-based access controls to restrict access and protect critical data.
3. Regularly Update and Patch Systems
Keep all software and systems up-to-date to protect against known vulnerabilities. Regular updates and patches are essential to close security gaps and defend against new threats.
4. Utilise Advanced Firewalls and Intrusion Detection Systems
Deploy firewalls to block unauthorised access and intrusion detection systems to monitor and respond to potential threats in real-time. These tools provide a robust defense against cyber attacks.
5. Educate and Train Your Employees
Security is a team effort. Regularly educate your employees about the latest cyber threats and best practices for maintaining security, such as recognising phishing attempts and following secure protocols.
6. Secure Mobile Devices and Remote Work Environments
Mobile devices and remote work setups should be protected with the same level of security as your main office. Use VPNs, encryption, and secure access protocols to safeguard data and communications.
7. Backup Data Regularly
Regularly backup your data to prevent loss in case of a cyberattack. Ensure that backups are encrypted and stored securely to protect against unauthorised access and data breaches. Take a look at our Comprehensive Cloud Back Up & Recovery solutions.
Leverage Advanced Security Tools
Another way to ensure effective network security is by using the correct tools. There are several amazing tools out there however, we use Lionguard which specializes in continuous attack surface management.
Liongard offers automated configuration change detection and detailed asset inventory, ensuring comprehensive visibility into your IT infrastructure. This tool helps detect misconfigurations, a common cause of cybersecurity issues, and provides timely alerts for swift resolutions.
By investing in the right tools, businesses can improve their security management, support compliance, and reduce the risk of cyber incidents, all while optimizing operational efficiency.
Conclusion
While it may not seem like a big deal, there have been several cases of businesses undergoing nightmare cyber threats, resulting in significant financial and reputational damage. That said, by conducting comprehensive audits, keeping systems updated, utilizing advanced security tools, and educating your team, you can create a more secure environment. If you need expert assistance and tailored solutions, reach out today! We’ll answer any questions you have on protecting your business.


1300 130 931
Level 57, 19-29 Martin Place, Sydney NSW 2000
Monday - Friday, 9:00 am - 5:00 pm
© Copyright 2025. Interdata Solutions Pty Limited. All rights reserved.